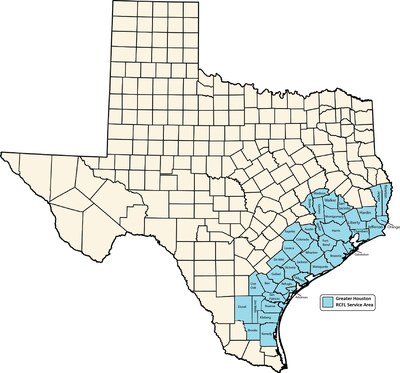
Greater Houston RCFL

 Upon request, the GHRCFL will provide computer forensics services to any law enforcement agency operating in our service area.
Upon request, the GHRCFL will provide computer forensics services to any law enforcement agency operating in our service area.
All law enforcement agencies with jurisdiction in the Greater Houston RCFL's service area are eligible to request and receive assistance - at no cost to them. The service area includes Harris County, and 39 southern counties in Texas covering the territory of Beaumont, Galveston, Huntsville, College Station, and Corpus Christi. When requesting assistance, please use the GHRCFL Service Request Form.
Participating Agencies
The Greater Houston RCFL is a unique partnership that promotes quality and strengthens computer forensics capacity. Computer forensics professionals from the following organizations are staffing the RCFL: